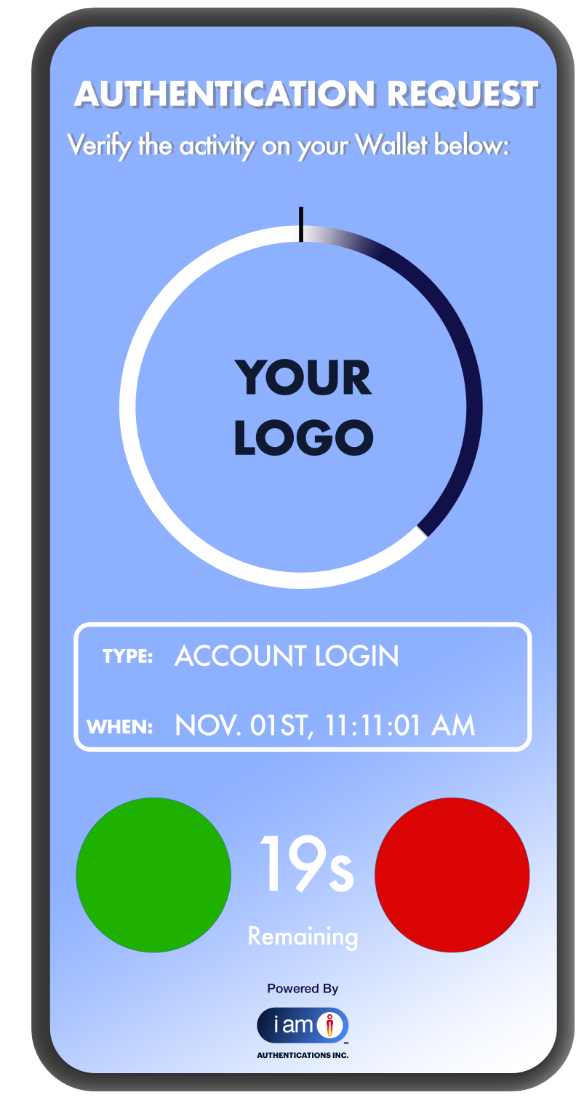
Push
Authentications:
The Command Center
Replace fragile, intercepted codes with high-fidelity authority. This encrypted, direct-to-device channel transforms passive logins into intentional acts of command. By eliminating vulnerable out-of-band signals, we ensure every approval is a conscious, informed, and secured decision.
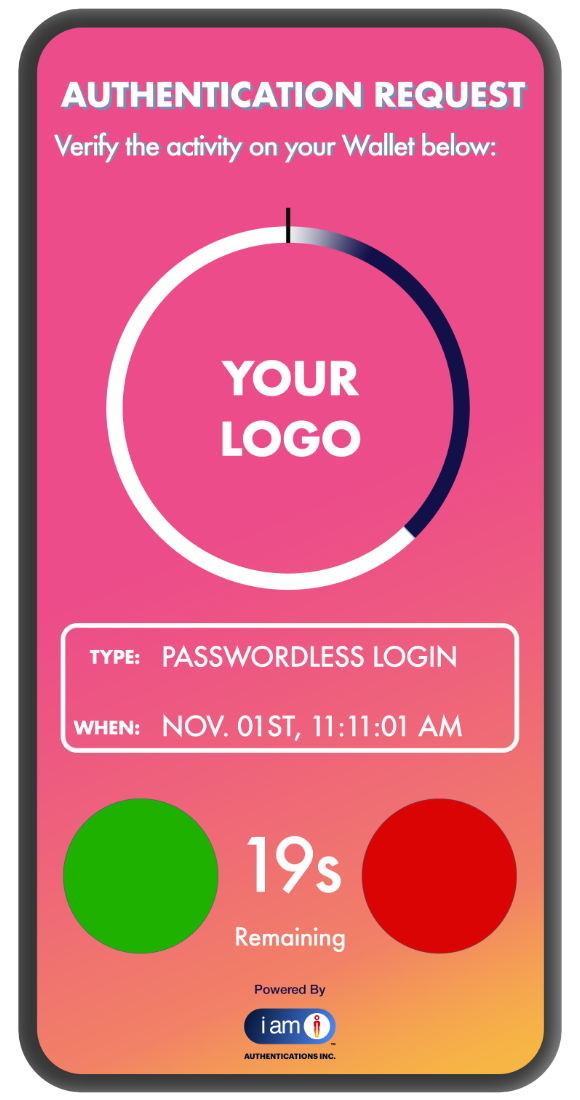
Passwordless
Authentications:
The Credential Sovereign
Neutralize the world’s largest attack surface by removing passwords entirely. This sophisticated, secret-free architecture kills phishing and credential stuffing at the source. Experience a streamlined, futuristic flow where your device is your identity and your intent is the only key.
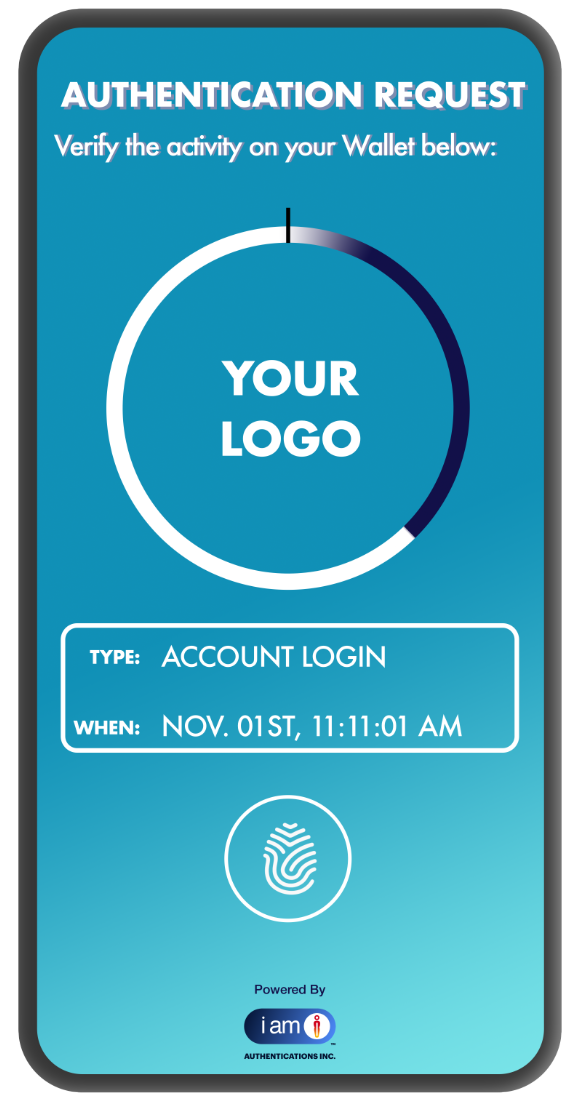
Biometric
Authentications:
The Biological Shield
Bridge digital intent with physical presence to create an impenetrable biological perimeter. By requiring a live biometric match for every push request, we effectively end MFA fatigue. Attackers can spam notifications, but they can never replicate the unique signature of the user.
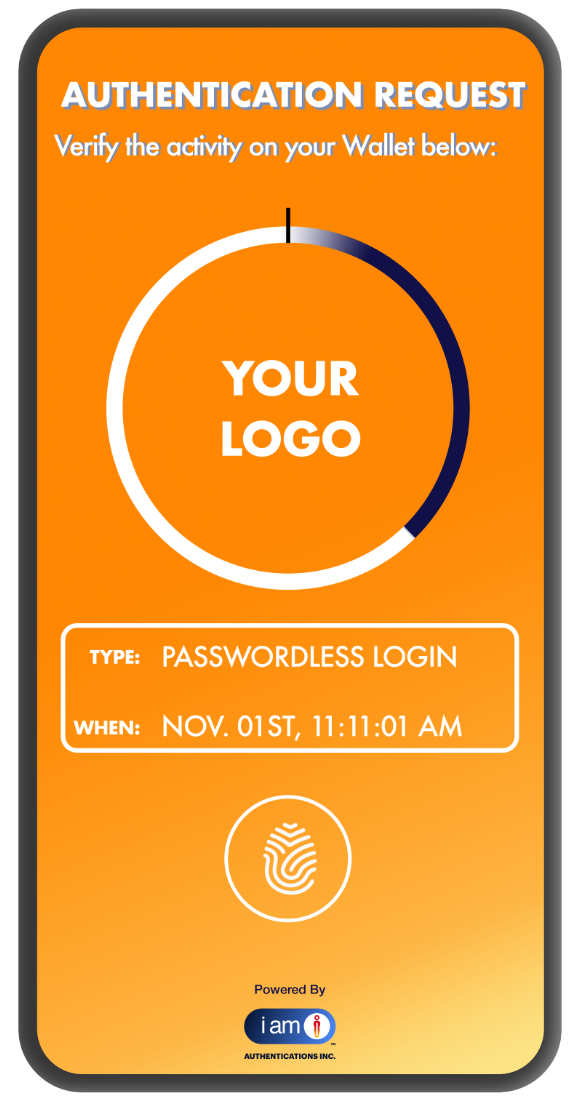
Biometric Passwordless Authentications:
The Apex of Defence
The gold standard for asset protection, merging zero-friction flow with absolute security. This phishing-impossible loop of "possession and being" renders session hijacking and social engineering obsolete. It is the definitive future of guardianship for high-value digital and financial ecosystems.
The IAmI Security Application is not a shared SaaS utility. It is deployed as a dedicated, private-tenant serverless instance designed to reside within your organization’s cloud boundary. This architecture ensures absolute data residency and eliminates the cross-contamination risks inherent in multi-tenant environments. By leveraging ephemeral compute, the instance scales elastically to meet request volume while maintaining a hardened, immutable execution state.

The I Am I integration process begins with an infrastructure audit. We do not provide a generic "out-of-the-box" solution; we engineer the authentication stack to align with your specific network topology, firewall configurations, and redundancy requirements. Our engineering team builds the bridge between our core protocol and your existing backend, ensuring zero-latency handshakes and seamless service discovery.
IAmI provides a complete suite of integration modules, including native SDKs for iOS and Android and pre-connected API endpoints for backend orchestration. These modules utilize advanced tokenization protocols to verify user intent without the requirement of PII extraction or ingestion. Developers can implement out-of-band verification directly into the application’s critical path, maintaining a frictionless user experience while enforcing high-entropy security.
IAmI's Admin Portal, with dashboard views and feature capabilities, enables you to view your customers' authentication events. You will find immutable activity logs (think sovereign receipts) directly within your private instance. Each log binds verified human intent to specific transaction metadata, fulfilling the rigorous requirements for non-repudiation under PSD3 and eIDAS 2.0. Because these forensic logs are generated and stored locally within your infrastructure, you maintain 100% authority over the audit trail with zero third-party visibility.
Unbreakable trustless authentication for Web3+ and Fintech. Zero PII. Total control. No legacy and vendor risks.
No central honeypots. Security is distributed, eliminating single points of failure and data trails.
Authenticate without exposing personal data. Only tokenized values—no PII, ever.
No static cookies. Attackers can’t clone sessions or impersonate users—ever.
Localized immutable audit trails and log events (Non-Repudiation).
Digital threats evolve by the second. We should connect to discuss how you can immediately fortify your customers’ accounts and safeguard their assets.
Whether you're ready to deploy or simply looking to explore the future of non-refutable security, let’s start a discovery session to secure your ecosystem before the next breach.
Reach out for "your" next-gen authentication service: IAmI Trustless MFA